
프로젝트에서 간단히 jwt를 이용한 로그인을 구현해 봤다!
🌱 Spring Security란?
인증(Authentication), 권한(Authorize) 부여 및 부호 기능을 제공하는 프레임워크이다.
인증 vs 인가
보통 인증 절차를 거친 후 인가 절차를 거친다.
인증
- 현재 유저가 누구인지 확인하는 과정 (로그인)
- 애플리케이션의 작업을 수행할 수 있는지 증명
인가
- 현재 유저의 권한을 검사하는 과정
- 페이지나 리소스 등에 접근할 수 있는지 검사
Spring Security 구조

1. Http Request 수신
사용자가 로그인 정보와 함께 인증 요청을 한다.
2. 유저 자격 기반으로 인증 토큰 생성
AuthenticationFilter가 요청을 가로채고, 가로챈 정보를 통해 UsernamePasswordAuthenticationToken의 인증용 객체를 생성한다.
3. Filter를 통해 AuthenticationToken을 AuthenticationManager로 위임
AuthenticationManager의 구현체인 ProviderManager에게 생성한 UsernamePasswordToken 객체를 전달한다.
4. AuthenticationProvider의 목록으로 인증 시도
AuthenticationManager는 등록된 AuthenticationProvider를 조회하며 인증을 요구한다.
5. UserDetailsService 요구
실제 데이터베이스에서 사용자 인증 정보를 가져오는 UserDetailsService에 사용자 정보를 넘겨준다.
6. UserDetails를 이용해 User 객체에 대한 정보 탐색
넘겨받은 사용자 정보를 통해 데이터베이스에서 찾아낸 사용자 정보인 UserDetails 객체를 만든다.
7. User 객체의 정보들을 UserDetails가 UserDetailsService(LoginService)로 전달
AuthenticationProvider들은 UserDetails를 넘겨받고 사용자 정보를 비교한다.
8. 인증 객체 or AuthenticationException
인증이 완료되면 권한 등의 사용자 정보를 담은 Authentication 객체를 반환한다.
9. 인증 완료
다시 최초의 AuthenticationFilter에 Authentication 객체가 반환된다.
10. SpringContext에 인증 객체 설정
Authentication 객체를 Security Context에 저장한다.
최종적으로는 SpringContext에 저장이 되고, 여기서는 세션/쿠키 방식을 사용하게 된다.
근데 우리는 jwt를 이용할 것이기 때문에 추가적인 코드 작업이 필요하다!
⚙️ 코드
1. 클라이언트 로그인
2. 정보 검증 후 access token/ refresh token 발급
3. refresh token은 redis에 저장 후 클라이언트에게 access token, refresh token 전달
4. access token이 만료되었으면 refresh token을 통해 access token, refresh token 재생성
JwtTokenProvider
- 유저 정보로 jwt access/refresh token 생성 및 재발급
- 토큰으로부터 유저 정보 받아옴
JwtFilter
- request 앞단에 붙이는 필터로 http request에서 토큰을 받아와 정상 토큰일 경우에 securityContext에 저장
JwtSecurityConfig
- JwtFilter를 Spring Security Filter Chain에 추가하기 위한 설정
SecurityConfig
- 스프링에서 기본적으로 필요한 시큐리티 설정
- jwt 적용 및 authentication 필요한 API 주소 설정
JwtAccessDeniedHandler
- 접근 권한 없을 때 403 에러
JwtAuthenticationEntryPoing
- 인증 정보 없을 때 401 에러
CorsConfig
- 서로 다른 서버 환경에서 자원을 공유하기 위해 필요한 설정
개발 환경
- SpringBoot 3.2.1
- Java 17
- Gradle
build.gradle 의존성 추가
implementation 'org.springframework.boot:spring-boot-starter-data-redis'
implementation 'org.springframework.boot:spring-boot-starter-security'
// JWT
implementation group: 'io.jsonwebtoken', name: 'jjwt-api', version: '0.11.5'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-impl', version: '0.11.5'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-jackson', version: '0.11.5'
application-security.yml
jwt:
#HS512 알고리즘을 사용할 것이기 때문에 512bit, 즉 64byte 이상의 secret key를 사용해야 한다.
secret: lkasjfljadakldjflkajefijalefjjahfglaiefjkleajdflkdklafjdskljflasjeifjaefjfdasfdagega
access-token-expire-time: 43200000 # 12시간
refresh-token-expire-time: 604800000 # 7일
RedisConfig
import org.springframework.beans.factory.annotation.Value;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.data.redis.connection.RedisConnectionFactory;
import org.springframework.data.redis.connection.lettuce.LettuceConnectionFactory;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.data.redis.serializer.StringRedisSerializer;
@Configuration
public class RedisConfig {
@Value("${spring.data.redis.port}")
private int port;
@Value("${spring.data.redis.host}")
private String host;
@Bean
public RedisConnectionFactory redisConnectionFactory() {
return new LettuceConnectionFactory(host, port);
}
@Bean
public RedisTemplate<String, String> redisTemplate() {
// redisTemplate를 받아와서 set, get, delete를 사용
RedisTemplate<String, String> redisTemplate = new RedisTemplate<>();
// setKeySerializer, setValueSerializer 설정
// redis-cli을 통해 직접 데이터를 조회 시 알아볼 수 없는 형태로 출력되는 것을 방지
redisTemplate.setKeySerializer(new StringRedisSerializer());
redisTemplate.setValueSerializer(new StringRedisSerializer());
redisTemplate.setConnectionFactory(redisConnectionFactory());
return redisTemplate;
}
}
JwtTokenProvider
import com.study.footprint.common.exception.CommonBadRequestException;
import io.jsonwebtoken.*;
import io.jsonwebtoken.io.Decoders;
import io.jsonwebtoken.security.Keys;
import lombok.extern.slf4j.Slf4j;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.stereotype.Component;
import java.security.Key;
import java.util.Arrays;
import java.util.Collection;
import java.util.Date;
import java.util.concurrent.TimeUnit;
import java.util.stream.Collectors;
@Slf4j
@Component
public class JwtTokenProvider {
private static final String AUTHORITIES_KEY = "auth";
private static final String BEARER_TYPE = "Bearer";
@Value("${jwt.access-token-expire-time}")
private long accessExpirationTime;
@Value("${jwt.refresh-token-expire-time}")
private long refreshExpirationTime;
private final Key key;
private final RedisTemplate<String, String> redisTemplate;
public JwtTokenProvider(@Value("${jwt.secret}") String secretKey, RedisTemplate<String, String> redisTemplate) {
byte[] keyBytes = Decoders.BASE64.decode(secretKey);
this.key = Keys.hmacShaKeyFor(keyBytes);
this.redisTemplate = redisTemplate;
}
// Access Token 생성
public String createAccessToken(Authentication authentication) {
// 권한들 가져오기
String authorities = authentication.getAuthorities().stream()
.map(GrantedAuthority::getAuthority)
.collect(Collectors.joining(","));
long now = (new Date()).getTime();
// Access Token 생성
Date accessTokenExpiresIn = new Date(now + accessExpirationTime);
return Jwts.builder()
.setSubject(authentication.getName()) // payload "sub": "name"
.claim(AUTHORITIES_KEY, authorities) // payload "auth": "ROLE_USER"
.setExpiration(accessTokenExpiresIn) // payload "exp": 151621022 (ex)
.signWith(key, SignatureAlgorithm.HS512) // header "alg": "HS512"
.compact();
}
// Refresh Token 생성
public String createRefreshToken(Authentication authentication) {
long now = (new Date()).getTime();
String refreshToken = Jwts.builder()
.setExpiration(new Date((new Date()).getTime() + refreshExpirationTime))
.signWith(key, SignatureAlgorithm.HS512)
.compact();
//redis 저장
redisTemplate.opsForValue().set(
authentication.getName(),
refreshToken,
refreshExpirationTime,
TimeUnit.MICROSECONDS
);
return refreshToken;
}
public Authentication getAuthentication(String accessToken) {
// 토큰 복호화
Claims claims = parseClaims(accessToken);
if (claims.get(AUTHORITIES_KEY) == null) {
throw new CommonBadRequestException("invalidToken");
}
// 클레임에서 권한 정보 가져오기
Collection<? extends GrantedAuthority> authorities =
Arrays.stream(claims.get(AUTHORITIES_KEY).toString().split(","))
.map(SimpleGrantedAuthority::new)
.collect(Collectors.toList());
// UserDetails 객체를 만들어서 Authentication 리턴
UserDetails principal = new User(claims.getSubject(), "", authorities);
return new UsernamePasswordAuthenticationToken(principal, "", authorities);
}
public boolean validateToken(String token) {
try {
Jwts.parserBuilder().setSigningKey(key).build().parseClaimsJws(token);
return true;
} catch (ExpiredJwtException e) {
log.info("만료된 JWT 토큰입니다.");
throw new CommonBadRequestException("expiredToken");
} catch (Exception e) {
log.info("유효하지 않은 JWT 토큰입니다.");
throw new CommonBadRequestException("invalidToken");
}
}
private Claims parseClaims(String accessToken) {
try {
return Jwts.parserBuilder().setSigningKey(key).build().parseClaimsJws(accessToken).getBody();
} catch (ExpiredJwtException e) {
return e.getClaims();
}
}
}
createAccessToken, createRefreshToken
- 유저 정보를 넘겨받아서 토큰을 생성한다.
- 넘겨받은 authentication의 getName() 메서드를 통해 username을 가져온다.
- 만료시간을 설정한다.
getAuthentication
- 토큰을 복호화하여 토큰에 들어있는 유저 정보를 꺼낸 후 authentication 객체를 반환한다.
validateToken
- 토큰 정보를 검증한다.
JwtFilter
import com.study.footprint.common.exception.CommonServerException;
import com.study.footprint.config.auth.JwtTokenProvider;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.data.redis.RedisConnectionFailureException;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.util.StringUtils;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
public class JwtFilter extends OncePerRequestFilter {
public static final String AUTHORIZATION_HEADER = "Authorization";
public static final String BEARER_PREFIX = "Bearer ";
private final JwtTokenProvider jwtTokenProvider;
public JwtFilter(JwtTokenProvider jwtTokenProvider) {
this.jwtTokenProvider = jwtTokenProvider;
}
// 실제 필터링 로직은 doFilterInternal 에 들어감
// JWT 토큰의 인증 정보를 현재 쓰레드의 SecurityContext 에 저장하는 역할 수행
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws IOException, ServletException {
//Request Header 에서 토큰을 꺼냄
String jwt = resolveToken(request);
try {
if (StringUtils.hasText(jwt) && jwtTokenProvider.validateToken(jwt)) {
Authentication authentication = jwtTokenProvider.getAuthentication(jwt);
SecurityContextHolder.getContext().setAuthentication(authentication);
}
} catch (RedisConnectionFailureException e) {
SecurityContextHolder.clearContext();
throw new CommonServerException("redisError");
} catch (Exception e) {
SecurityContextHolder.clearContext();
throw new CommonServerException("invalidToken");
}
filterChain.doFilter(request, response);
}
// Request Header 에서 토큰 정보를 꺼내오기
private String resolveToken(HttpServletRequest request) {
String bearerToken = request.getHeader(AUTHORIZATION_HEADER);
if (StringUtils.hasText(bearerToken) && bearerToken.startsWith(BEARER_PREFIX)) {
return bearerToken.split(" ")[1].trim();
}
return null;
}
}
OncePerRequestFilter
- 인터페이스를 구현하기 때문에 요청받을 때 단 한 번만 실행된다.
doFilterInternal
- 실제 필터링 로직을 수행한다.
- Request Header에서 Access Token을 꺼내고 유저 정보를 꺼내 SecurityContext에 저장한다.
- SecurityConfig에서 권한 체크가 필요하지 않다고 정의한 것 이외의 모든 요청은 이 필터를 거치기 때문에 토큰 정보가 없거나 유효하지 않다면 정상적으로 수행되지 않는다.
resolveToken
- Request Header에서 토큰 정보를 꺼내오기 위한 메서드이다.
JwtSecurityConfig
import com.study.footprint.config.auth.filter.JwtFilter;
import org.springframework.security.config.annotation.SecurityConfigurerAdapter;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.web.DefaultSecurityFilterChain;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
// 직접 만든 TokenProvider 와 JwtFilter 를 SecurityConfig 에 적용할 때 사용
public class JwtSecurityConfig extends SecurityConfigurerAdapter<DefaultSecurityFilterChain, HttpSecurity> {
private final JwtTokenProvider jwtTokenProvider;
public JwtSecurityConfig(JwtTokenProvider jwtTokenProvider) {
this.jwtTokenProvider = jwtTokenProvider;
}
// TokenProvider 를 주입받아서 JwtFilter 를 통해 Security 로직에 필터를 등록
@Override
public void configure(HttpSecurity http) {
JwtFilter customFilter = new JwtFilter(jwtTokenProvider);
http.addFilterBefore(customFilter, UsernamePasswordAuthenticationFilter.class);
}
}- SecurityConfigurerAdapter <DefaultSecurityFilterChain, HttpSecurity> 인터페이스를 구현하는 구현체이다.
- 직접 만든 JwtFilter를 Security Filter 앞에 추가한다.
JwtAuthenticationEntryPoint
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.stereotype.Component;
import java.io.IOException;
@Component
public class JwtAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence (HttpServletRequest request, HttpServletResponse response,
AuthenticationException authException) throws IOException, ServletException {
// 유효한 자격증명을 제공하지 않고 접근하려 할때 401
response.sendError(HttpServletResponse.SC_UNAUTHORIZED);
}
}- 사용자 정보가 잘못되거나, 토큰이 유효하지 않은 경우 401 에러를 발생시킨다.
JwtAccessDeniedHandler
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import org.springframework.security.access.AccessDeniedException;
import org.springframework.security.web.access.AccessDeniedHandler;
import org.springframework.stereotype.Component;
import java.io.IOException;
@Component
public class JwtAccessDeniedHandler implements AccessDeniedHandler {
@Override
public void handle (HttpServletRequest request, HttpServletResponse response,
AccessDeniedException accessDeniedException) throws IOException, ServletException {
// 필요한 권한이 없이 접근하려 할때 403
response.sendError(HttpServletResponse.SC_FORBIDDEN);
}
}- 필요한 권한이 존재하지 않은 경우 403 에러를 발생시킨다.
CorsConfig
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.cors.CorsConfiguration;
import org.springframework.web.cors.UrlBasedCorsConfigurationSource;
import org.springframework.web.filter.CorsFilter;
@Configuration
public class CorsConfig {
@Bean
public CorsFilter corsFilter() {
UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();
CorsConfiguration config = new CorsConfiguration();
config.setAllowCredentials(true); //내 서버가 응답할 때 json 자바 스크립트 허용
config.addAllowedOrigin("*"); //포트번호 응답 다름 허용
config.addAllowedHeader("*"); //헤더 값 응답 허용
config.addAllowedMethod("*"); //메서드 응답 허용
source.registerCorsConfiguration("/**", config); //모든 url에 대하여 위 들을 적용시키겠다.
return new CorsFilter(source);
}
}- 프론트엔드, 백엔드를 구분지어서 개발하거나 서로 다른 서버 환경에서 자원을 공유할 때 설정한다.
- Cors 설정이 안 되어있으면 오류가 발생한다.
SecurityConfig
import com.study.footprint.config.auth.JwtSecurityConfig;
import com.study.footprint.config.auth.JwtTokenProvider;
import com.study.footprint.config.auth.handler.JwtAccessDeniedHandler;
import com.study.footprint.config.auth.handler.JwtAuthenticationEntryPoint;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.method.configuration.EnableMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configurers.AbstractHttpConfigurer;
import org.springframework.security.config.annotation.web.configurers.HeadersConfigurer;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
import org.springframework.web.filter.CorsFilter;
@EnableWebSecurity
@EnableMethodSecurity
@Configuration
public class SecurityConfig {
private final JwtTokenProvider jwtTokenProvider;
private final JwtAuthenticationEntryPoint jwtAuthenticationEntryPoint;
private final JwtAccessDeniedHandler jwtAccessDeniedHandler;
private final CorsFilter corsFilter;
public SecurityConfig(JwtTokenProvider jwtTokenProvider, CorsFilter corsFilter,
JwtAuthenticationEntryPoint jwtAuthenticationEntryPoint,
JwtAccessDeniedHandler jwtAccessDeniedHandler) {
this.jwtTokenProvider = jwtTokenProvider;
this.corsFilter = corsFilter;
this.jwtAuthenticationEntryPoint = jwtAuthenticationEntryPoint;
this.jwtAccessDeniedHandler = jwtAccessDeniedHandler;
}
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.httpBasic(AbstractHttpConfigurer::disable)
.csrf(AbstractHttpConfigurer::disable) // token을 사용하므로 csrf 보안이 필요없으므로 disable 처리
.formLogin(AbstractHttpConfigurer::disable)
.addFilterBefore(corsFilter, UsernamePasswordAuthenticationFilter.class)
.exceptionHandling(config -> config
.authenticationEntryPoint(jwtAuthenticationEntryPoint)
.accessDeniedHandler(jwtAccessDeniedHandler)
)
.headers(header -> header.frameOptions(HeadersConfigurer.FrameOptionsConfig::disable))
.authorizeHttpRequests(
registry -> registry.requestMatchers("/", "v1/join/**", "v1/login/**", "v1/reissue", "/profile", "/css/**","/images/**","/js/**","/h2-console/**","/favicon.ico")
.permitAll()
.anyRequest()
.authenticated()
)
// 세션을 사용하지 않기 때문에 STATELESS로 설정
.sessionManagement(sessionManagement ->
sessionManagement.sessionCreationPolicy(SessionCreationPolicy.STATELESS))
// JwtFilter를 addFilterBefore로 등록했던 JwtSecurityConfig 클래스를 적용
.with(new JwtSecurityConfig(jwtTokenProvider), customizer -> {});
return http.build();
}
}
SecurityUtil
import com.study.footprint.common.exception.CommonBadRequestException;
import lombok.extern.slf4j.Slf4j;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
@Slf4j
public class SecurityUtil {
private SecurityUtil() { }
// SecurityContext 에 유저 정보가 저장되는 시점
// Request 가 들어올 때 JwtFilter 의 doFilter 에서 저장
public static Long getCurrentMemberId() {
final Authentication authentication = SecurityContextHolder.getContext().getAuthentication();
if (authentication == null || authentication.getName() == null) {
throw new CommonBadRequestException("authenticationInfoNotFound");
}
return Long.parseLong(authentication.getName());
}
}- JwtFilter에서 세팅한 유저 정보를 꺼낸다.
- MemberId를 저장했기 때문에 Long 타입으로 반환한다.
- SecurityContext는 사용자의 정보를 저장한다.
CustomUserDetailsService
import com.study.footprint.common.exception.CommonNotFoundException;
import com.study.footprint.domain.member.Member;
import com.study.footprint.domain.member.MemberRepository;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import org.springframework.transaction.annotation.Transactional;
import java.util.Collections;
@Transactional(readOnly = true)
@Service
public class CustomUserDetailsService implements UserDetailsService {
private final MemberRepository memberRepository;
public CustomUserDetailsService(MemberRepository memberRepository) {
this.memberRepository = memberRepository;
}
@Override
@Transactional
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
return memberRepository.findByEmail(username)
.map(this::createUserDetails)
.orElseThrow(() -> new CommonNotFoundException("userNotFound"));
}
// DB 에 User 값이 존재한다면 UserDetails 객체로 만들어서 리턴
private UserDetails createUserDetails(Member member) {
GrantedAuthority grantedAuthority = new SimpleGrantedAuthority(member.getRole().toString());
return new User(
String.valueOf(member.getId()),
member.getPassword(),
Collections.singleton(grantedAuthority)
);
}
}- loadUserByUsername 메서드를 오버라이드하는데 여기서 넘겨받은 UserDetails랑 Authentication의 패스워드를 비교하고 검증한다.
- DB에 User값이 존재하면 UserDetails 객체를 만들어서 리턴한다.
AuthService
import com.study.footprint.common.exception.CommonBadRequestException;
import com.study.footprint.common.response.SingleResult;
import com.study.footprint.config.auth.JwtTokenProvider;
import com.study.footprint.dto.member.request.LoginReqDto;
import com.study.footprint.dto.member.request.TokenReqDto;
import com.study.footprint.dto.member.response.LoginResDto;
import com.study.footprint.dto.member.response.TokenResDto;
import com.study.footprint.service.common.ResponseService;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.core.Authentication;
import org.springframework.stereotype.Service;
import org.springframework.transaction.annotation.Transactional;
@Transactional(readOnly = true)
@Service
public class AuthService {
private final AuthenticationManagerBuilder authenticationManagerBuilder;
private final ResponseService responseService;
private final JwtTokenProvider jwtTokenProvider;
private final RedisTemplate<String, String> redisTemplate;
public AuthService(AuthenticationManagerBuilder authenticationManagerBuilder, ResponseService responseService,
JwtTokenProvider jwtTokenProvider, RedisTemplate<String, String> redisTemplate) {
this.authenticationManagerBuilder = authenticationManagerBuilder;
this.responseService = responseService;
this.jwtTokenProvider = jwtTokenProvider;
this.redisTemplate = redisTemplate;
}
@Transactional
public SingleResult<LoginResDto> login(LoginReqDto loginReqDto) {
// 1. Login ID/PW 를 기반으로 AuthenticationToken 생성
UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(loginReqDto.getEmail(), loginReqDto.getPassword());
// 2. 실제로 검증 (사용자 비밀번호 체크) 이 이루어지는 부분
// authenticate 메서드가 실행이 될 때 CustomUserDetailsService 에서 만들었던 loadUserByUsername 메서드가 실행됨
Authentication authentication = authenticationManagerBuilder.getObject().authenticate(authenticationToken);
// 3. 인증 정보를 기반으로 JWT 토큰 생성
LoginResDto loginResDto = LoginResDto.builder()
.accessToken(jwtTokenProvider.createAccessToken(authentication))
.refreshToken(jwtTokenProvider.createRefreshToken(authentication))
.build();
return responseService.getSingleResult(loginResDto);
}
@Transactional
public SingleResult<TokenResDto> reissue(TokenReqDto tokenReqDto) {
// Refresh Token 검증
jwtTokenProvider.validateToken(tokenReqDto.getRefreshToken());
// Access Token 에서 Member ID 가져오기
Authentication authentication = jwtTokenProvider.getAuthentication(tokenReqDto.getAccessToken());
// 저장소에서 Member ID 를 기반으로 Refresh Token 값 가져옴
String refreshToken = redisTemplate.opsForValue().get(authentication.getName());
// Refresh Token 일치하는지 검사
if (!refreshToken.equals(tokenReqDto.getRefreshToken())) {
throw new CommonBadRequestException("invalidRefreshToken");
}
// 새로운 토큰 생성
TokenResDto tokenResDto = TokenResDto.builder()
.accessToken(jwtTokenProvider.createAccessToken(authentication))
.refreshToken(jwtTokenProvider.createRefreshToken(authentication))
.build();
return responseService.getSingleResult(tokenResDto);
}
}
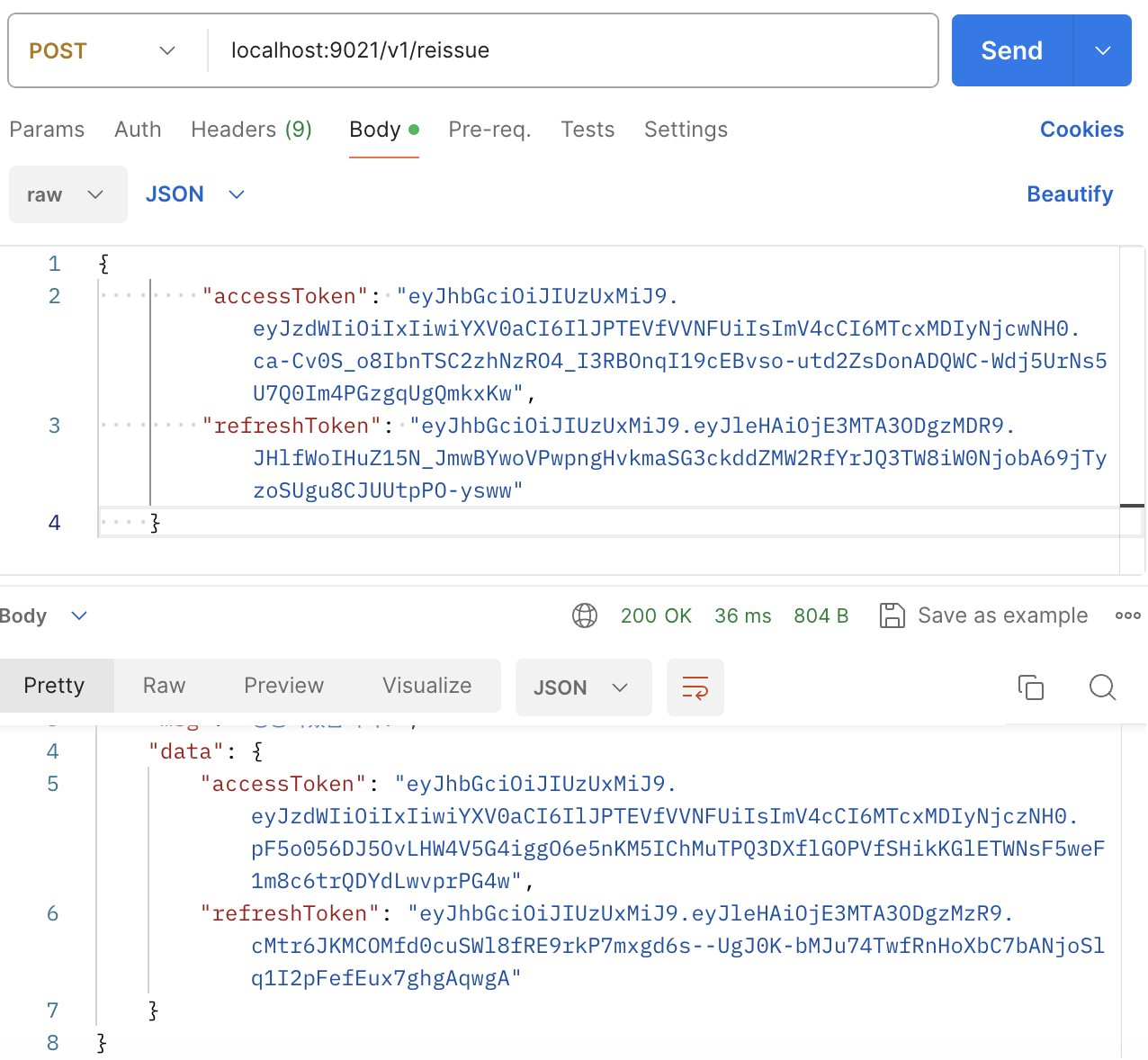
결과화면


reference
https://9keyyyy.tistory.com/48
https://kimtaesoo99.tistory.com/118
'Spring' 카테고리의 다른 글
| [Spring] @PrePersist와 @PreUpdate (0) | 2024.03.16 |
|---|---|
| [Spring] N+1 문제와 fetch join 해결 및 테스트 (0) | 2024.03.15 |
| [Spring] @AllArgsConstructor, @RequiredArgsConstructor 사용을 지양한 이유 (0) | 2024.03.05 |
| [Spring] @ExceptionHandler를 통한 예외 처리 (+ DTO Validation) (0) | 2024.03.05 |
| [Spring] MessageSource를 이용한 국제화 exception 적용하기 (0) | 2024.03.02 |
